Popular WordPress plugin JetPack locks you out of your WordPress site after updating. Although unexpected and therefore annoying, it is apparently JetPack and nothing more sinister. [1]
I already have been using two different plugins (not JetPack) to block brute force hacking attempts. This plus a possibly non-intuitive approach to controlling user credentials eliminated prior issues I had with break in attempts.
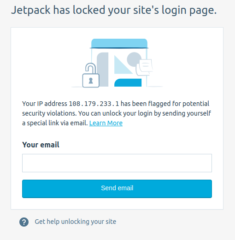
The message you get when you try to login looks more like a phishing attack after your site has been hacked: for me, this was scary – it looked like JetPack had been compromised. It is actually a clumsy way JetPack is trying to force you to turn on one setting, and easily solved.
I have no idea what happens if you go through all the nonsense to “sending yourself a special link” (doesn’t THAT sound trustworthy!) by entering your email (which does NOT make sense as WordPress ALREADY HAS YOUR EMAIL from your profile): This sounds very much like a hack and scam. Any upgrade requiring a settings change should simply send you an email immediately following the upgrade.
My approach to solving this problem, took two (2) minutes. Simply:
- to log in to my hosting server and rename …./wp-content/plugins/jetpack to xjetpack, (WordPress will disable the JetPack plugin because it is now ‘not found’)
- then again browse to my home page and again click login – login proceeds normally to login as an administrator
- back on the hosting server rename …/wp-content/plugins/xjetpack back to jetpack
- and finally in WordPress go to plugins and “Activate” the JetPack plugin, then click Settings under the JetPack plugin.
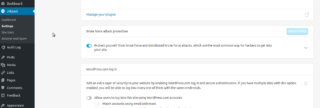
- The screen capture below is the section of the Setting for JetPack that the plugin wants you to turn on, and it is turned on for you once you “Activate” the plugin again. TURN THIS SETTING OFF. Problem solved. You may resume working.
[1] “Brute Force” attacks are where a hostile system tries to guess your password through trial and error. This kind of attack is continuous – once a server is on-line criminal systems all over the planet try this constantly. If you have a username such as “admin” or “Bob” then it is merely a matter of time until they find the password (and you probably deserve to be hacked).
Detection of “brute force” attacks is generally agreed to look for more than one attempt to log in! For example, after 5 failed logins the server (or a WordPress plugin) would lock the account, sending an email to the address in the user’s profile. The user then knows a hack on the account has been attempted and the user must then take steps to reset the password in order to restore access.
The problem with this JetPack update is 1) it turns on the “security” feature without your foreknowledge and consent, and 2) it forces failure on every login attempt, not after some chosen number of failed login attempts. By failing all administrator login attempts regardless of their validity the feature becomes a liability.
I recommend that you 1) turn off the JetPack “Brute Force” protection feature until it works, and 2) use other mature plugins, such as WordFence, to catch brute force attacks and many other kinds of attacks, as one example, requesting a non-existing page. JetPack will likely detect and correct their error fairly soon as it is a very active plugin.